
Legit Official
Product & Engineering Blog
The official blog of Onetime Secret - Behind-the-scenes insights from the team building Onetime Secret.
Follow our journey as we share operational challenges, deployment stories, product updates, and technical
decisions. From UI improvements to infrastructure changes, we're documenting our experiences building and
maintaining a privacy-focused message sharing platform.






Engineering
Domain Strategy Reengineered: Building Verification into Our Architecture
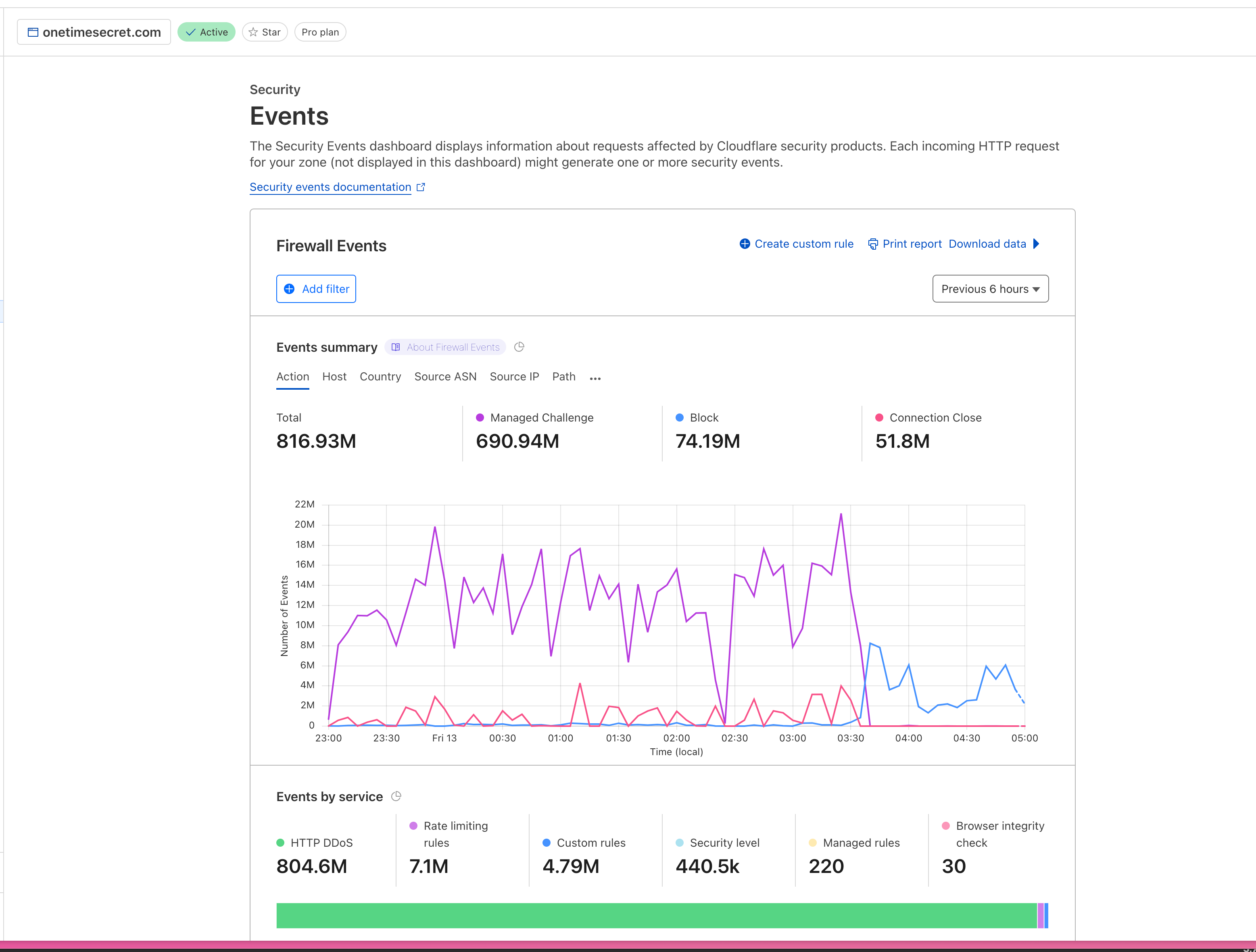
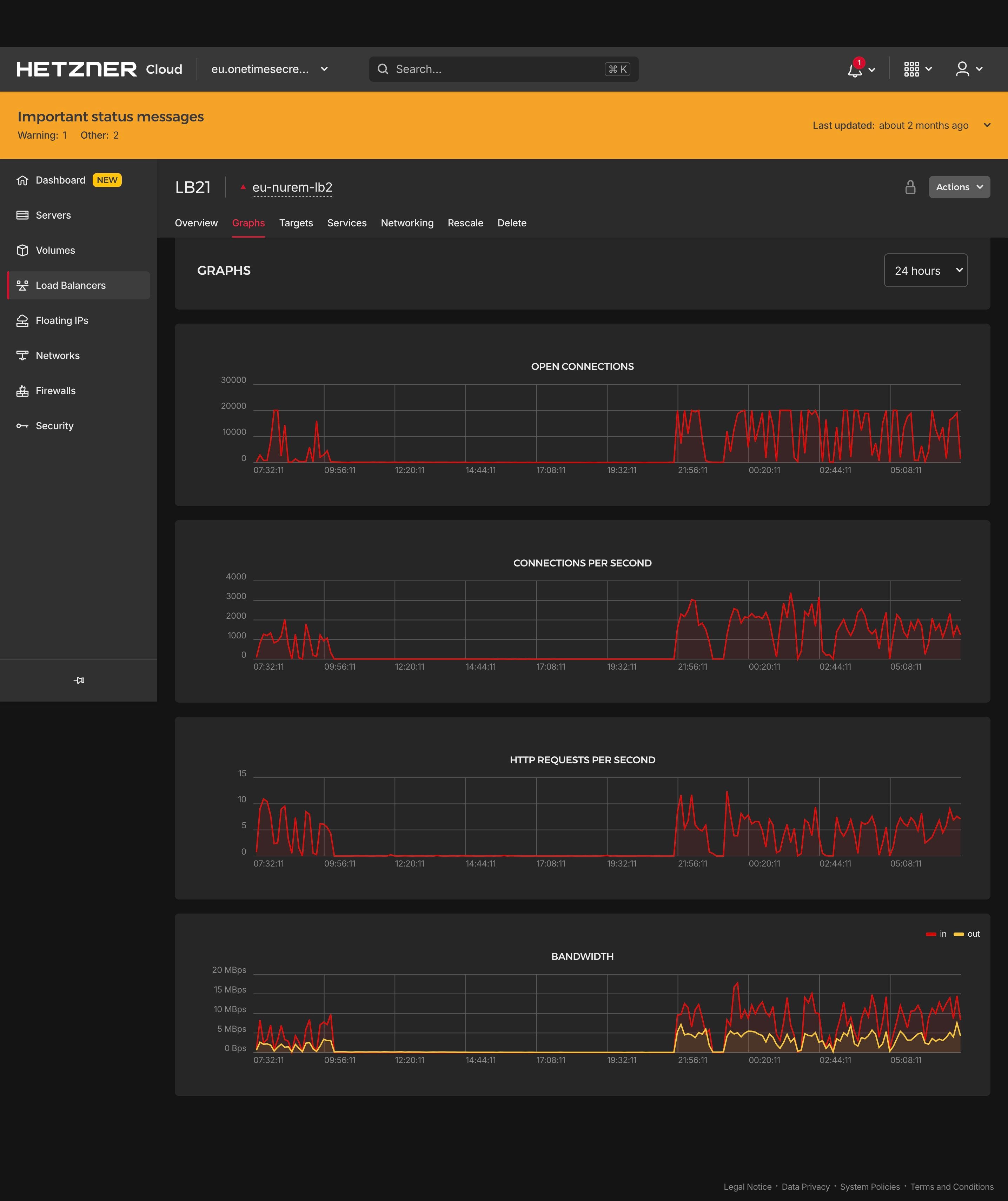
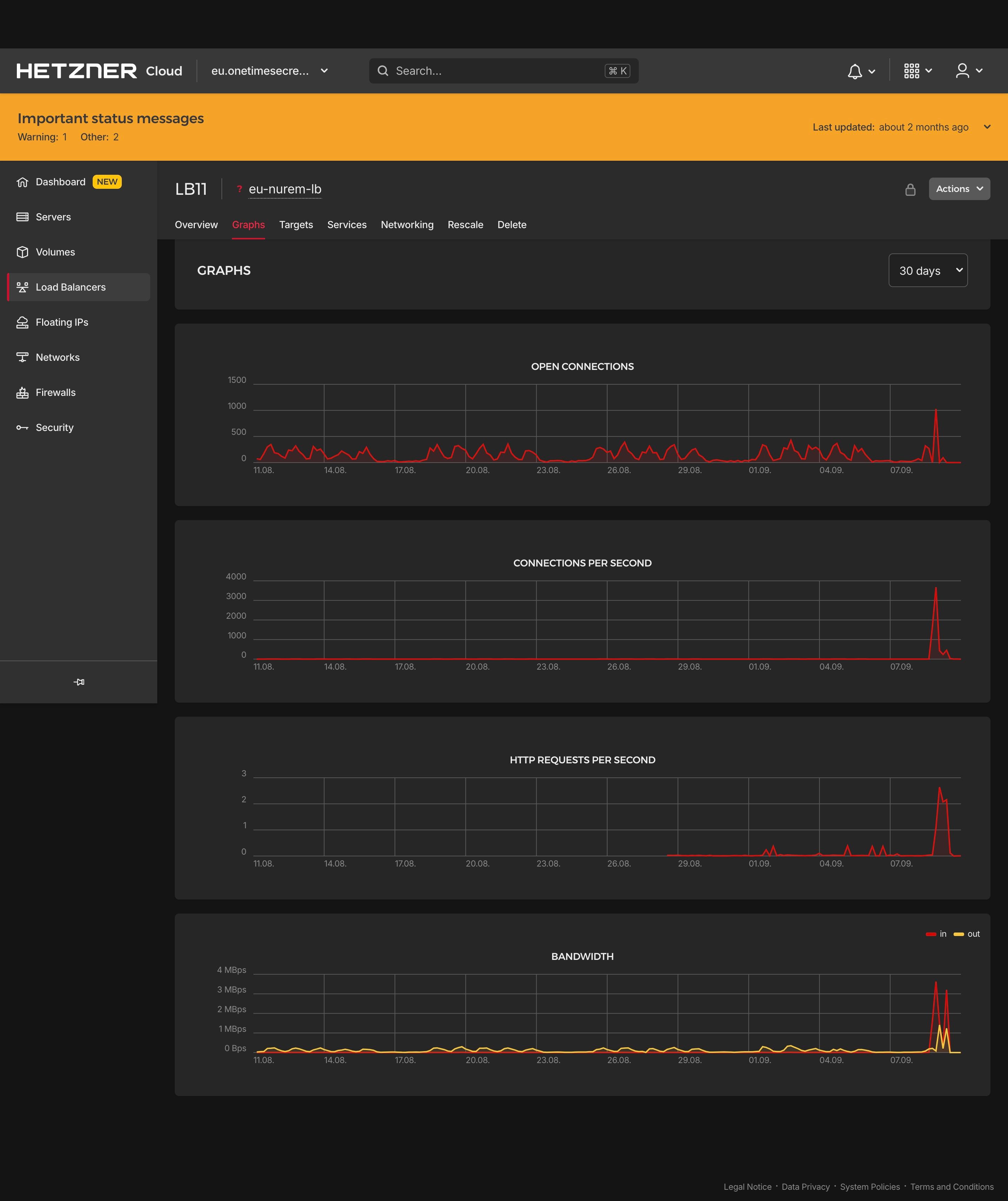
A recent phishing attempt exposed users to an impostor site that mirrored our interface but actually exposed secrets. While Cloudflare helped shut down this particular site, the incident highlighted a broader concern: user can struggle to distinguish legitimate from fraudulent services (see Which one of these is the real onetimesecret?).

Operations
Homepage Update: We're Going Regional
OnetimeSecret.com has been around for quite a while – long enough to attract several impostor sites ranging from confusingly similar to downright malicious. Thanks to our alert users and partners (like in this recent GitHub issue), we can spot and address these problems.






Company
Industry Practices We Deliberately Avoid
At Onetime Secret, we believe privacy and simplicity go hand in hand. While many services collect extensive user data, we've chosen a different path focused on what matters most: secure, reliable secret sharing. You can learn more about our guiding principles in our documentation.

Feature
Expanding Horizons: Introducing US Data Locality for Onetime Secret
We're jazzed to introduce our new US locality, enhancing our data privacy options and expanding user choice. The US instance is now available at us.onetimesecret.com, complementing our existing EU site at eu.onetimesecret.com.


Guide
Installing Onetime Secret: The Complete Guide (Part 1 of 5)
Welcome to our comprehensive series on setting up and installing Onetime Secret. In this first installment, we'll walk you through the process of installing Onetime Secret as a standalone web application using the latest methods and best practices. Whether you're a seasoned sysadmin or just getting started with self-hosting, this guide will help you get Onetime Secret up and running smoothly.




Privacy
Data Privacy Regulations: A New Framework for UI Design
The current landscape of user interface design faces challenges similar to those of the late 1990s. Dial-up speeds, small screens (desktop included), and limited browser capabilities were the constraints of that era. Today's constraints, however, are not technical limitations but data privacy regulations like GDPR and CCPA. These regulations provide an opportunity to improve UI design.

Onetime
Open-Source First Development Model
At Onetime Secret, we believe in transparency and community-driven development. Our open-source first approach ensures that all new features and improvements benefit our entire user base, from individual developers to enterprise customers. This post outlines our development model, its benefits, and how it shapes our business strategy.

Best-Practices
Copying server data from the command-line, safely
All of times I've found myself in a situation where I need to get a little bit of data on to or off of a server somewhere. Copy & paste works in some cases but not always. Another option is a service like Pastebin but it's not cool for sensitive info like config files because even though you can easily forget to delete them when you're done.
Best-Practices
'Good' vs 'Strong' passwords
One of my pet peeves about security is people who advocate for 'strong' passwords. Everyone knows these people; they're the tech support person who tells you your password must have a minimum number of characters that you only use when censoring expletives. Even worse, some of them use a random password generator to assign a password to you that you're unable to change. The argument for this is that if you have a wider range of characters in your password, you have greater entropy and therefore it is harder for your password to be hacked. While there is some truth to that, there are numerous flaws in the logic when using it to determine a good security policy:
C

